Bacros.A
Summary
Bacros.A is a virus that infects local filesystem files by renaming all text files (.txt) as exe. It can also copy itself in floppies and CD-roms. The virus also drops and executes a Word Macro virus W97M/Bacros.A.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The binary virus is written in Borland Deplhi and its body size is 356352 bytes.
Both the binary and the macro parts are designed to work together but they can replicate independently.
Typical symptom for end users is that they find some of their images being replaced with a pictures that says "KUOLE JEHOVA".
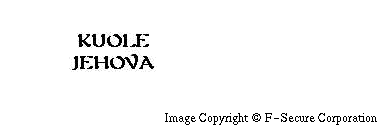
It was found in the wild in the beginning of September 2004.
Installation to system
If run without arguments, for example double-clicking it, it installs itself to system. First it makes three copies of itself in Windows system directory:
%WinSysDir%\mssys.exe %WinSysDir%\sys.exe %WinSysDir%\msdosdrv.exe
Then it adds the following keys in registry:
[HKLM\Software\Microsoft\Windows\CurrentVersion\Run] "MSSys" = "%WinSysDir%\mssys.exe -d" [HKCU\Software\Microsoft\Windows\CurrentVersion\Run] "MSDosdrv" = "%WinSysDir%\msdosdrv.exe -t"
With these registry keys, the virus is activated in the next boot. The program behaves differently depending on the argument (-d or -t).
It also tries to display a text file with the name of the binary (for example, if the binary name is "tiedotteet.exe", text file it tries to display is "tiedotteet.txt"). If the text file doesn't exist, the binary displays a text file that contains the filename of the virus repeated several times.
Writing the Word document
When run via the registry with argument -t (MSDosdrv), the program drops a Word document infeted with W97M/Bacros.A virus in two places: to user's personal documents folder and in %SystemRoot% folder with the name "WordInfo.doc". It also tries to disable the MS Office macro virus protection in the registry.
Spreading in Word document
When run via the registry with argument -d (MSSys), the program check the date of the system. If the day of the month is 10th, 20th or 30th, the virus tries to open the infected with W97M/Bacros.A file:
%SystemRoot%\WordInfo.doc
This macro virus replicated during opening and closing document. It resides in a macro called 'NewBacros' and uses Organizer Copy method to replicate. It infects Notmal.Dot and also creates a copy of itself in Normal.Doc in MS Word's template folder.
If the day of the month is 6th it types a text:
I, Madman
and changes the application user name to:
ANCIENT
In an attempt to spread the binary part with itself to flopies, W97M/Bacros.A tries to copy the binary virus from 'C:\Windows\System\sys.exe' to the root of A: drive as ReadMy.exe. It does this when the macro virus is executed from a A: drive.
Spreading in CD-roms
If the day of the month is any other day, it tries to copy itself on CD-rom drive with the name "ReadMy.exe". It also writes an Autorun.inf file on CD-rom for automatic execution of the file. The program checks for the drive id (CDROM) so it won't work with other removable devices, for example USB-sticks. The CD-rom writing works only if the machine has packet-writing capabilites, for example Nero InCD.
Renaming text files
If the day of the month is 2nd, the virus scans through all local disk drives and makes a copy of itself with the name of every text file (.txt) it founds.
The icon of these EXE files looks like the default icon of a TXT file:
Replacing picture files
If the day of the month is 1st, the virus scans through all local disk drives and replaces all gif-files it finds with a copy of a small gif-file showing the text "Kuole Jehova". This is finnish and means "Die Jehovah".
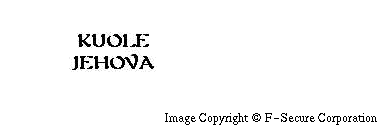
Changing the background picture
If the date is 6th of December (Finland's independence day), the virus sets a small Finland flag as a background picture of the system.

Deleting files
If the date is 25th of December (1st christmas day), the virus deletes all files on all local hard drives.