Apropos
Summary
Apropos uses highly sophisticated stealth techniques to avoid detection.
The spyware collects the browsing habits of users and system information and sends it back to ContextPlus servers. Targeted pop-up advertisements are displayed while browsing the Web.
Removal
Based on the settings of your F-Secure security product, it may block the file from running, move it to the quarantine where it cannot spread or cause harm, or ask you to select an action.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
PeopleOnPage produces the Apropos family of spyware.
It uses the same ContextPlus engine as the public software POP!, made by PeopleOnPage. However, the Apropos branch uses a silent installer and rootkit techniques to hide itself from detection. When the client connects to the server, the name Apropos is used as the client name.
ContextPlus gathers an extensive amount of information from the user's computer. The application tracks which software is installed, what web sites are visited, and the user's browsing behavior. Each installation is given a unique ID, which is sent to the ContextPlus server to request a pop-up advertisement.
Rootkit Details
Apropos contains a kernel-mode rootkit that allows it to hide files, directories, registry keys, and processes. The rootkit is implemented by a kernel-mode driver which starts automatically early in the boot process. When the files and registry keys have been hidden, no user-mode process is allowed to access them.
Installation
Apropos installs itself into a randomly named directory under the Program Files folder.
Additional, it installs one randomly named executable file (.EXE) into the Windows\System32 folder and one randomly named driver (.SYS) into the Windows\System32\Drivers folder.
The following two log files generated by the F-Secure security product illustrate this behavior:
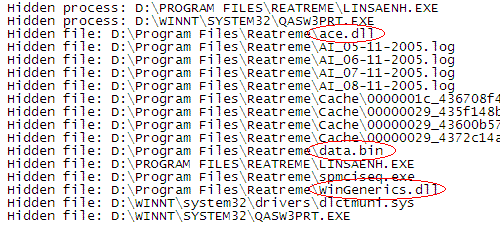
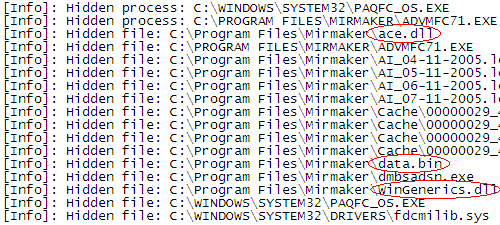
In addition to the randomly named files, Apropos uses several statically named files that reside in the installation directory, such as ace.dll, data.bin and WinGenerics.dll. Also, the log files and cache files are easy to recognize.
Hiding Technique
The kernel-mode driver patches the kernel at a very deep level. Important data structures and several Native API functions implemented by the kernel are modified. Specifically, the following functions are patched:
- NtCreateKey
- NtOpenKey
- NtEnumerateKey
- IoCreateFile
- NtQueryDirectoryFile
- NtQuerySystemInformation
The operating system uses these functions to gain access to, and information about, files, directories, registry keys, and processes.
Additional Note
Apropos is not associated with Apropos Technologies, Inc (NASDAQ: APRS).